单线ADSL带宽4M,线路损耗后实际速度3.5M左右,上传350k左右,由于ADSL满速下载、上传速度会变慢,配置ROS最高上传、下载不得超过总带宽90%,QOS配置如下:
首先分类标记上传、下载数据:
#https://www.haiyun.me
/ip firewall mangle
#小数据
add chain=prerouting action=mark-connection new-connection-mark=Small-conn passthrough=yes protocol=icmp comment=Small
add chain=prerouting action=mark-connection new-connection-mark=Small-conn passthrough=yes protocol=udp dst-port=53
add chain=postrouting action=mark-connection new-connection-mark=Small-conn passthrough=yes protocol=udp dst-port=53
add chain=prerouting action=mark-connection new-connection-mark=Small-conn passthrough=yes protocol=udp dst-port=123
add chain=postrouting action=mark-packet new-packet-mark=Small-up passthrough=no out-interface=pppoe-out1 connection-mark=Small-conn
add chain=prerouting action=mark-packet new-packet-mark=Small-up passthrough=no in-interface=bridge-local connection-mark=Small-conn
add chain=prerouting action=mark-packet new-packet-mark=Small-down passthrough=no in-interface=pppoe-out1 connection-mark=Small-conn
#SSH及VPN
add chain=prerouting action=mark-connection new-connection-mark=SSH-conn passthrough=yes protocol=tcp dst-port=22 comment=SSH
add chain=prerouting action=mark-connection new-connection-mark=SSH-conn passthrough=yes protocol=tcp dst-port=23
add chain=prerouting action=mark-packet new-packet-mark=SSH-up passthrough=no in-interface=bridge-local connection-mark=SSH-conn
add chain=prerouting action=mark-packet new-packet-mark=SSH-down passthrough=no in-interface=pppoe-out1 connection-mark=SSH-conn
#网页数据
add chain=prerouting action=mark-connection new-connection-mark=HTTP-conn passthrough=yes protocol=tcp dst-port=80 comment=HTTP
add chain=prerouting action=mark-connection new-connection-mark=HTTP-conn passthrough=yes protocol=tcp dst-port=443
add chain=prerouting action=mark-packet new-packet-mark=HTTP-up passthrough=no in-interface=bridge-local connection-mark=HTTP-conn
add chain=prerouting action=mark-packet new-packet-mark=HTTP-down passthrough=no in-interface=pppoe-out1 connection-mark=HTTP-conn
#其它
add chain=prerouting action=mark-connection new-connection-mark=Other-conn passthrough=yes comment=Other
add chain=prerouting action=mark-packet new-packet-mark=Other-up passthrough=no in-interface=bridge-local connection-mark=Other-conn
add chain=prerouting action=mark-packet new-packet-mark=Other-down passthrough=no in-interface=pppoe-out1 connection-mark=Other-conn
新建队列类型为PCQ:
#pcq-rate为每个了数据流最大速度,0为按数据流数公平分配带宽,pcq-limit为每一数据流队列长度;
#pcq-total-limit不能小于内网主机数*pcq-limit。
/queue type
add name="Small-down" kind=pcq pcq-rate=0 pcq-limit=50 pcq-classifier=dst-address pcq-total-limit=2000
add name="Small-up" kind=pcq pcq-rate=50k pcq-limit=50 pcq-classifier=src-address pcq-total-limit=2000
add name="SSH-down" kind=pcq pcq-rate=0 pcq-limit=50 pcq-classifier=dst-address pcq-total-limit=2000
add name="SSH-up" kind=pcq pcq-rate=50k pcq-limit=50 pcq-classifier=src-address pcq-total-limit=2000
add name="HTTP-down" kind=pcq pcq-rate=0 pcq-limit=50 pcq-classifier=dst-address pcq-total-limit=2000
add name="HTTP-up" kind=pcq pcq-rate=80k pcq-limit=50 pcq-classifier=src-address pcq-total-limit=2000
add name="Other-down" kind=pcq pcq-rate=0 pcq-limit=50 pcq-classifier=dst-address pcq-total-limit=2000
add name="Other-up" kind=pcq pcq-rate=30k pcq-limit=50 pcq-classifier=src-address pcq-total-limit=2000
添加队列树调用之前标记的数据包设置优先级,队列类型设置为之前新建的PCQ类型。
/queue tree
add name="Parent-up" parent=global-out limit-at=330k max-limit=330k
add name="Parent-down" parent=global-in limit-at=3300k max-limit=3300k
add name=Small-up parent=Parent-up packet-mark=Small-up limit-at=70k max-limit=150k queue=Small-up priority=1
add name=Small-down parent=Parent-down packet-mark=Small-down limit-at=500k max-limit=1000k queue=Small-down priority=1
add name=SSH-up parent=Parent-up packet-mark=SSH-up limit-at=70k max-limit=200k queue=SSH-up priority=2
add name=SSH-down parent=Parent-down packet-mark=SSH-down limit-at=500k max-limit=1000k queue=SSH-down priority=2
add name=HTTP-up parent=Parent-up packet-mark=HTTP-up limit-at=150k max-limit=200k queue=HTTP-up priority=3
add name=HTTP-down parent=Parent-down packet-mark=HTTP-down limit-at=2000k max-limit=3000k queue=HTTP-down priority=3
add name=Other-up parent=Parent-up packet-mark=Other-up limit-at=20k max-limit=80k queue=Other-up priority=4
add name=Other-down parent=Parent-down packet-mark=Other-down limit-at=200k max-limit=2000k queue=Other-down priority=4
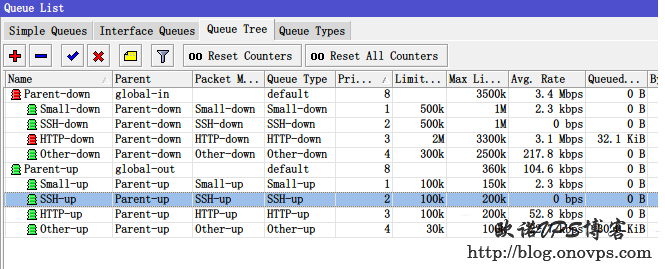
ROS路由设置HTB+PCQ流量控制的一些注意事项:
1.WAN限制上传,按源地址分组;LAN限制下载,按目标地址分组;
2.passthrough是否继续向下匹配此链接,选择yes会向下匹配,下面规则如有匹配标记会改变;
3.在HTB首先满足Limit At,在父级有剩余带宽的前提下才会Max Limit,优先级高的队列优先获得Max Limit;
4.mark-connection的数据包是双向的,然后通过mark-pack区分上传和下载;
5.global-in在DNAT后,global-out在SNAT前,分别可匹配目标地址和源地址。
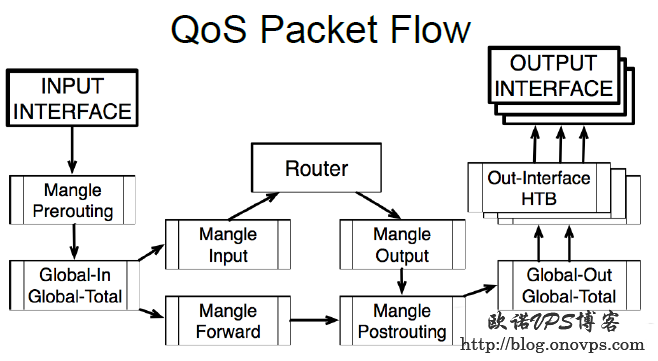
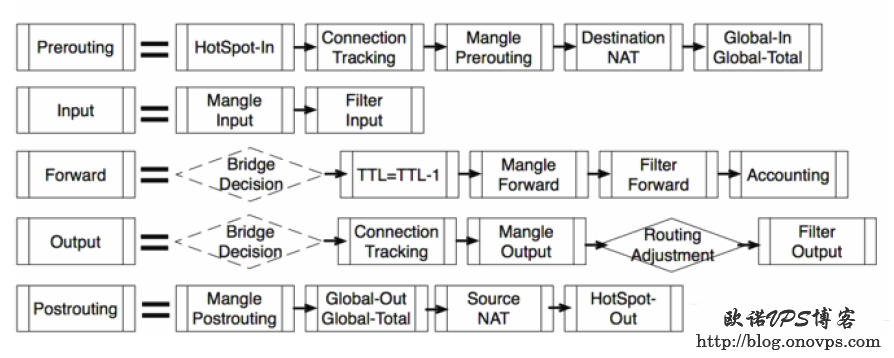
ROS数据包流程图: