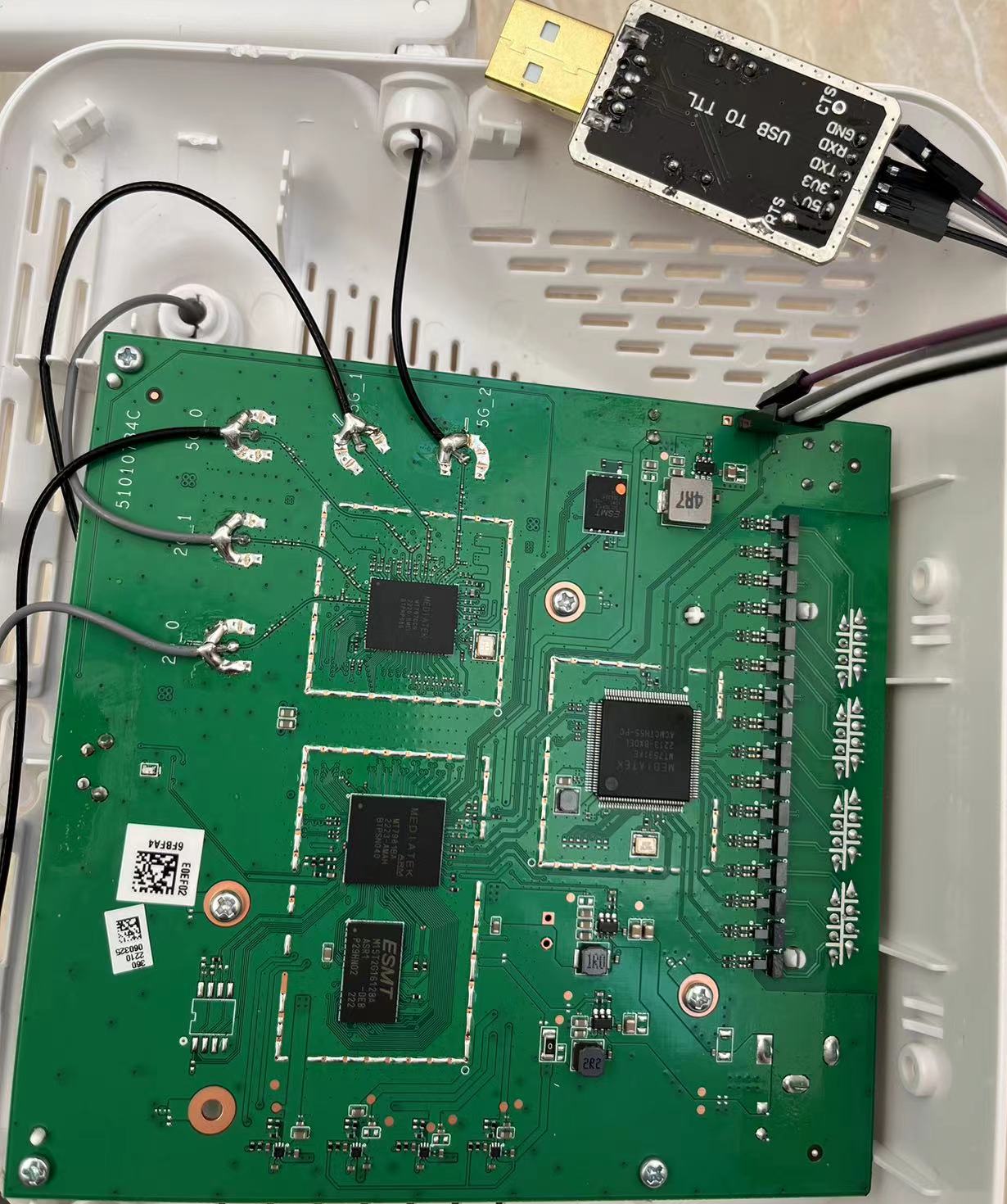
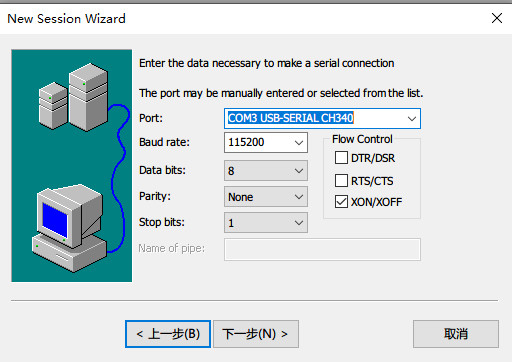
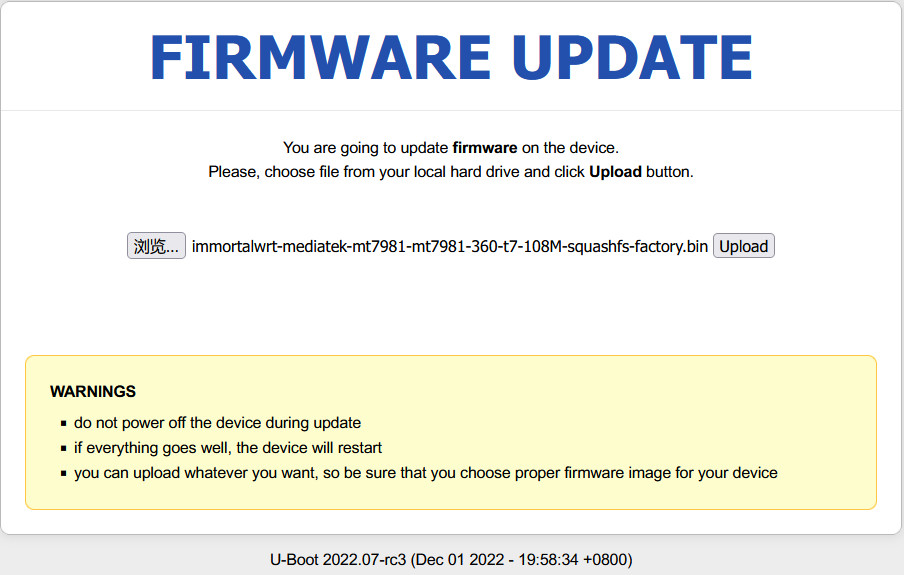
下载mips musl交叉编译环境,也可以使用https://toolchains.bootlin.com/,也可使用openwrt提供的openwrt-toolchain-armsr-armv8_gcc_musl。
wget https://musl.cc/mips-linux-musl-cross.tgz
tar zxf mips-linux-musl-cross.tgz
export PATH=$PATH:`pwd`/mips-linux-musl-cross/bin/编译ncurses,后续要将/lib/terminfo/x/xterm-256color等复制到目标机器/data/terminfo目录,不然运行tmux提示找不到terminfo database。
wget https://ftp.gnu.org/pub/gnu/ncurses/ncurses-6.4.tar.gz
tar zxf ncurses-6.4.tar.gz
cd ncurses-6.4/
./configure --prefix /usr/local/tmux --with-default-terminfo-dir=/data/terminfo --enable-pc-files --host=mips-linux-musl
#解决错误:strip: Unable to recognise the format of the input file `/usr/local/tmux/bin/tic'
ln -s `pwd`/../mips-linux-musl-cross/bin/mips-linux-musl-strip /usr/local/bin/strip
make && make install
rm -rf /usr/local/bin/strip编译libevent和tmux:
wget https://github.com/libevent/libevent/releases/download/release-2.1.12-stable/libevent-2.1.12-stable.tar.gz
tar zxf libevent-2.1.12-stable.tar.gz
cd libevent-2.1.12-stable/
./configure --prefix /usr/local/tmux --host=mips-linux-musl --disable-openssl
make && make install
wget https://github.com/tmux/tmux/releases/download/3.3a/tmux-3.3a.tar.gz
tar zxf tmux-3.3a.tar.gz
cd tmux-3.3a/
export CFLAGS="-I/usr/local/tmux/include -I/usr/local/tmux/include/ncurses"
export LDFLAGS="-L/usr/local/tmux/lib"
./configure --enable-static --prefix=/usr/local/tmux --host=mips-linux-musl
make && make install静态编译dropbear,当前最新版本使用SRT关闭窗口后dropbear和执行的命令一直在后台不结束,使用dropbear-2020.81版本正常。
wget https://github.com/mkj/dropbear/archive/refs/tags/DROPBEAR_2020.81.tar.gz
tar zxf DROPBEAR_2020.81.tar.gz
cd dropbear-DROPBEAR_2020.81/
#老版本没有configure使用autoconf生成
./configure --enable-static --prefix=/usr/local/dropbear --host=mips-linux-musl --disable-zlib --disable-syslog --disable-harden --disable-lastlog --disable-utmp --disable-utmpx --disable-wtmp --disable-wtmpx --disable-pututline --disable-pututxline --disable-loginfunc
PROGRAMS="dropbear dbclient dropbearkey dropbearconvert scp" MULTI=1 make strip编译前可修改default_options.h定义dropbear运行时的PATH用来查找scp执行文件,sftp-server执行文件路径使用SFTP。
#define SFTPSERVER_PATH "/data/bin/sftp-server"
#define DROPBEAR_PATH_SSH_PROGRAM "/data/bin/dbclient"
#define DEFAULT_ROOT_PATH "/usr/sbin:/usr/bin:/sbin:/bin:/data/bin"
#define DEFAULT_PATH "/usr/bin:/bin:/data/bin"编译的为单个文件dropbearmulti,使用时创建软链接:
ln -s /data/bin/dropbearmulti /data/bin/dropbear
ln -s /data/bin/dropbearmulti /data/bin/dropbearkey
ln -s /data/bin/dropbearmulti /data/bin/scp 使用:
mkdir /etc/dropbear/
./dropbearkey -t ecdsa -s 256 -f /etc/dropbear/dropbear_ecdsa_host_key
./dropbearkey -t ed25519 -f /etc/dropbear/dropbear_ed25519_host_key
./dropbearkey -t dss -f /etc/dropbear/dropbear_dss_host_key
./dropbearkey -t rsa -s 3072 -f /etc/dropbear/dropbear_rsa_host_key
./dropbear -r /etc/dropbear/dropbear_rsa_host_key静态编译openssl/openssh/sshd:
wget https://github.com/madler/zlib/releases/download/v1.2.13/zlib-1.2.13.tar.gz
tar zxf zlib-1.2.13.tar.gz
cd zlib-1.2.13/
CC=mips-linux-musl-gcc ./configure --prefix=/usr/local/openssh --static
make && make install
wget https://github.com/openssl/openssl/releases/download/OpenSSL_1_1_1t/openssl-1.1.1t.tar.gz
tar zxf openssl-1.1.1t.tar.gz
cd openssl-1.1.1t
#./config no-asm no-shared --prefix=/usr/local/openssh --cross-compile-prefix=mips-linux-musl-
#sed -i 's/-m64//g' Makefile
./Configure linux-mips32 no-asm no-shared --prefix=/usr/local/openssh --cross-compile-prefix=mips-linux-musl-
make && make install
export CFLAGS="-I/usr/local/openssh/include/"
export LDFLAGS="-L/usr/local/openssh/lib/"
wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.3p1.tar.gz
tar zxf openssh-9.3p1.tar.gz
cd openssh-9.3p1/
./configure --prefix=/usr/local/openssh --host=mips-linux-musl --with-ldflags=-static --disable-lastlog --disable-utmp --disable-utmpx --disable-wtmp --disable-wtmpx --disable-libutil --disable-pututline --disable-pututxline --with-default-path=/usr/bin:/bin:/usr/sbin:/sbin:/sbin:/usr/sbin:/bin:/usr/bin:/data/bin
make && make install使用:
mkdir /etc/ssh
ssh-keygen -A
cat <<EOF > /etc/ssh/sshd.conf
Port 22
PermitRootLogin yes
ChallengeResponseAuthentication no
Subsystem sftp /data/bin/sftp-server
PubkeyAuthentication yes
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
EOF
/src/openssh-9.3p1/sshd -f /etc/ssh/sshd.conf静态编译bash:
wget https://ftp.gnu.org/gnu/bash/bash-5.1.tar.gz
tar zxf bash-5.1.tar.gz
cd bash-5.1/
./configure --enable-static-link --host=mips-linux-musl --without-bash-malloc
make
mips-linux-musl-strip -s bash静态编译iperf3:
wget https://github.com/esnet/iperf/releases/download/3.15/iperf-3.15.tar.gz
tar zxf iperf-3.15.tar.gz
cd iperf-3.15/
./configure --prefix=/usr/local/iperf3 --host=mips-linux-musl "LDFLAGS=--static" --disable-shared
make静态编译dnsmasq:
wget https://thekelleys.org.uk/dnsmasq/dnsmasq-2.89.tar.gz
tar zxf dnsmasq-2.89.tar.gz
cd dnsmasq-2.89/
CC=mips-linux-musl-gcc make CFLAGS=-Os LDFLAGS=-staticEcoNet EN751221 SOC MIPS 34Kc uclibc编译vnstat:
#gcc版本太高vnstat编译失败,由于目标是uclibc,使用上面的musl编译后不能运行
wget https://toolchains.bootlin.com/downloads/releases/toolchains/mips32/tarballs/mips32--uclibc--stable-2022.08-1.tar.bz2
tar jxf mips32--uclibc--stable-2022.08-1.tar.bz2
export PATH=$PATH:`pwd`/mips32--uclibc--stable-2022.08-1/bin/
wget https://www.sqlite.org/2025/sqlite-autoconf-3490100.tar.gz
tar zxf sqlite-autoconf-3490100.tar.gz
cd sqlite-autoconf-3490100/
./configure --host=mips-linux --disable-shared --enable-static --prefix=/usr/local/sqlite
make && make install
cd ../
wget https://humdi.net/vnstat/vnstat-2.13.tar.gz
tar zxf vnstat-2.13.tar.gz
cd vnstat-2.13/
CPPFLAGS="-I/usr/local/sqlite/include/" LDFLAGS="-L/usr/local/sqlite/lib/ -static" ./configure --host=mips-linux --disable-shared --enable-static --prefix=/usr/local/vnstat
make && make install编译aarch64版本coreutils,内核版本4.1.52:
wget https://toolchains.bootlin.com/downloads/releases/toolchains/aarch64/tarballs/aarch64--glibc--stable-2018.11-1.tar.bz2
tar jxf aarch64--glibc--stable-2018.11-1.tar.bz2
export PATH=$PATH:`pwd`/aarch64--glibc--stable-2018.11-1/bin/wget http://ftp.gnu.org/gnu/coreutils/coreutils-8.30.tar.xz
tar Jxf coreutils-8.30.tar.xz
cd coreutils-8.30/
./configure --host=aarch64-linux --prefix=/usr/local/coreutils