实现流程:Cacti服务器安装syslog-ng为中央日志服务器,Cacti通过syslog插件展示,从服务器通过网络将日志实时发送到中央日志服务器。
Cacti下syslog插件安装:
#https://www.haiyun.me
cd /home/wwwroot/cacti/plugins/
wget -O syslog.tar.gz http://docs.cacti.net/_media/plugin:syslog-v1.22-2.tgz
tar zxvf syslog.tar.gz
新建syslog数据库并授权:
mysql -u root -p
create database syslog;
grant all privileges on syslog.* to cacti@localhost;
导入syslog数据库:
mysql -u root -p syslog < syslog/syslog.sql
修改syslog插件配置文件,然后通过web界面安装syslog插件,略过。
vim syslog/config.php
$use_cacti_db = false; #不使用cacti默认数据库
#定义syslog数据库信息
if (!$use_cacti_db) {
$syslogdb_type = 'mysql';
$syslogdb_default = 'syslog';
$syslogdb_hostname = 'localhost';
$syslogdb_username = 'cactiuser';
$syslogdb_password = 'password';
$syslogdb_port = 3306;
Cacti服务器端安装syslog-ng服务端,yum安装需先安装epel源。
yum -y install syslog-ng
service syslog stop
chkconfig syslog off
service syslog-ng start
chkconfig syslog-ng on
编辑syslog-ng配置文件添加以下内容:
vim /etc/syslog-ng/syslog-ng.conf
source net { #源设备为网络接收数据
udp();
};
destination d_mysql { #目的操作
pipe("/tmp/mysql.pipe"
template("INSERT INTO syslog_incoming (host, facility, priority, date, time, message) VALUES ( '$HOST', '$FACILITY', '$PRIORITY', '$YEAR-$MONTH-$DAY', '$HOUR:$MIN:$SEC', '$MSG' );\n")
template-escape(yes)
);
};
log { source(net); destination(d_mysql); };
#log { source(s_sys); destination(d_mysql); };
新建日志数据库导入脚本:
vim /etc/syslog-ng/syslog.sh
#!/bin/bash
if [ ! -e /tmp/mysql.pipe ]; then
mkfifo /tmp/mysql.pipe
fi
while [ -e /tmp/mysql.pipe ]
do
mysql -u root --password=passwd syslog < /tmp/mysql.pipe
done
启动脚本并配置开机启动:
sh /etc/syslog-ng/syslog.sh &
echo "sh /etc/syslog-ng/syslog.sh" >> /etc/rc.local
从服务器配置syslog将日志发送到syslog-ng服务器:
echo "*.* @server" >> /etc/syslog.conf
/etc/init.d/syslog restart
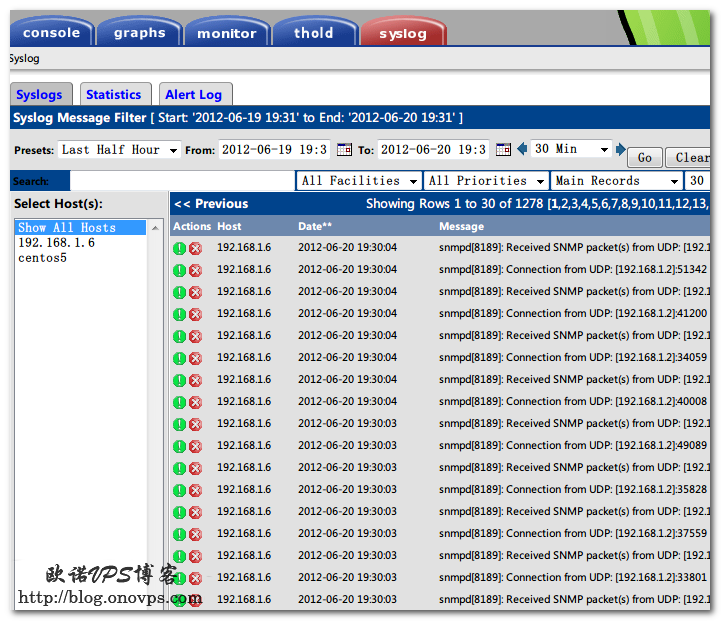
上张效果图: